Introduction
Imagine a world where verifying your qualifications, medical records, or travel documents is as simple as a single click. That’s exactly what verified credentials bring to the table.
In today’s fast-paced digital world, where trust and efficiency are essential, verified credentials are paving the way for a future where outdated, paper-heavy processes are replaced by secure, seamless interactions.
These digital game-changers aren’t just about convenience—they’re about building a transparent and efficient system that works for everyone. From job seekers and employers to students and universities, verified credentials are reshaping the way we think about trust and verification.
What Are Verified Credentials?
Verified credentials function as digital passports for your achievements and records, providing a modern, secure way to showcase your qualifications. These credentials, issued by trusted entities like universities, employers, or government bodies, are designed to be tamper-proof and easy to share.
Picture this: you’re applying for a job, but instead of emailing copies of your certificates or waiting weeks for a recruiter to verify your degree, you share your verified credentials instantly. The employer can authenticate them in seconds, eliminating delays and building trust right from the start.
This seamless process benefits both individuals and organizations, reducing administrative hurdles while ensuring accuracy and security. Verified credentials are transforming traditional verification methods, making them faster, more reliable, and infinitely more convenient.

World Wide Web Consortium’s (W3C) Verified Credentials Data Model
The W3C’s Verified Credentials Data Model is a foundational framework that ensures digital credentials are secure, interoperable, and universally accepted. By standardizing how these credentials are issued, stored, and shared, it creates a seamless system for verification across borders, benefiting both individuals and organizations.
-
Global Standardization: The framework provides a uniform structure for digital credentials, ensuring they are tamper-proof and consistent regardless of the issuing authority. This guarantees that credentials meet a reliable and globally recognized format.
-
Interoperability: Credentials issued using this model can operate across various platforms, applications, and systems. This compatibility simplifies integration into different workflows, whether for hiring, education, or healthcare.
-
Simplified Cross-Border Verification: With the W3C model, credentials issued in one country can be easily verified in another. This eliminates the need for lengthy authentication processes and promotes smoother international operations.
-
Enhanced Trust: By using cryptographic proofs and decentralized systems, the model builds trust in the authenticity of credentials, ensuring that they are not falsified or tampered with.
-
Support for Innovation: The framework provides a solid foundation for developers and organizations to create innovative tools, such as digital wallets and blockchain-based verification systems, further enhancing the utility of verified credentials.
Benefits of Verified Credentials
The benefits of verified credentials go beyond convenience—they’re about empowerment, efficiency, and trust. They simplify life for individuals and make organizations more productive, all while enhancing security.
Benefits for Individuals
Verified credentials empower individuals by giving them full control over their records instead of relying on universities, employers, or other organizations for verification. Individuals can access their credentials instantly and share them securely. Whether it’s for a job application, visa processing, or even a medical checkup, the process becomes seamless and stress-free, with built-in trust ensuring widespread acceptance. Even when attaching a cover letter to a job application, verified credentials help strengthen your case—letting you back up claims with instant, trusted proof of qualifications.
- Ownership of Records: Individuals have complete control over their credentials without relying on third parties for access or verification.
- Instant Sharing: Share verified records in seconds for any purpose, such as job applications or travel documentation.
- Streamlined Processes: Eliminate delays and inefficiencies traditionally associated with credential verification.
- Security and Trust: Credentials are tamper-proof and easily verifiable, building confidence with recipients.
- Multi-Purpose Utility: Suitable for various scenarios like education, healthcare, and employment.
Benefits for Organizations
With instantly verifiable and tamper-proof records, organizations can trust the accuracy of the information they receive. This not only minimizes the risk of fraud but also enables them to focus on core priorities like hiring top talent or improving service delivery.
- Efficiency Gains: Reduces the need for manual verification, saving time and administrative effort.
- Fraud Prevention: Ensures information is tamper-proof, minimizing the risk of forged credentials.
- Trust Building: Verifiable records create confidence in the hiring process or service delivery.
- Resource Optimization: Allows organizations to focus on strategic goals instead of routine checks.
- Enhanced Decision-Making: Provides reliable data for better hiring or operational decisions.
Why Verified Credentials Matter?
In today’s fast-paced, digital-first world, traditional verification systems are struggling to keep up. Long wait times, costly processes, and vulnerability to fraud make these systems inefficient and unreliable.
From job applications to loan approvals, the manual back-and-forth of document verification creates frustration for individuals and organizations alike. Verified credentials step in to solve these inefficiencies. They offer a streamlined, secure, and tamper-proof way to share and verify records.
By leveraging advanced technologies like blockchain and decentralized identifiers, these credentials ensure trust, transparency, and speed. Whether it’s applying for a job, enrolling in a university, or crossing borders, verified credentials provide a solution that’s both future-ready and user-friendly.
Problems With Traditional Verification Systems
Let’s face it: traditional verification methods have been a source of frustration for years. Waiting weeks for official transcripts to arrive, navigating endless email threads or calls to verify someone’s credentials, or dealing with outdated systems is inefficient and time-consuming.
These methods not only slow down processes like hiring or admissions but also lead to significant administrative overhead. Moreover, with paper-based records, there’s always the looming risk of fraud, errors, or even loss, further complicating the situation.
Verified credentials revolutionize this entire process by introducing a digital, tamper-proof solution. Instead of relying on slow, manual verification systems, these credentials enable instant sharing and authentication.
This eliminates delays, significantly reduces costs, and minimizes the chances of fraud or mistakes. By leveraging advanced technologies like blockchain, verified credentials bring a level of security, transparency, and efficiency that traditional systems simply can’t match.
Whether it’s for academic, professional, or personal records, verified credentials set a new standard for trust and reliability.
How Verified Credentials Work
The process of verified credentials revolves around secure issuance, ownership, and verification. Here’s a step-by-step overview:
-
Credential Issuance: A trusted organization, such as a university or employer, creates a digital credential for an individual. This credential includes secure cryptographic proofs to ensure its authenticity.
-
Storage and Ownership: The credential is handed over to the individual, who becomes its owner. They can store it in a secure digital wallet designed for verified credentials, ensuring they have complete control.
-
Sharing for Verification: When the individual needs to present their credential—be it for a job application, visa process, or healthcare requirement—they can share it with the verifier digitally, using a simple and secure process.
-
Instant Authentication: The verifier checks the credential’s authenticity through cryptographic proofs stored on decentralized systems like blockchain, eliminating the need for manual checks or intermediary processes.
This system not only makes verification fast and hassle-free but also ensures that all parties can trust the integrity of the credentials being shared.
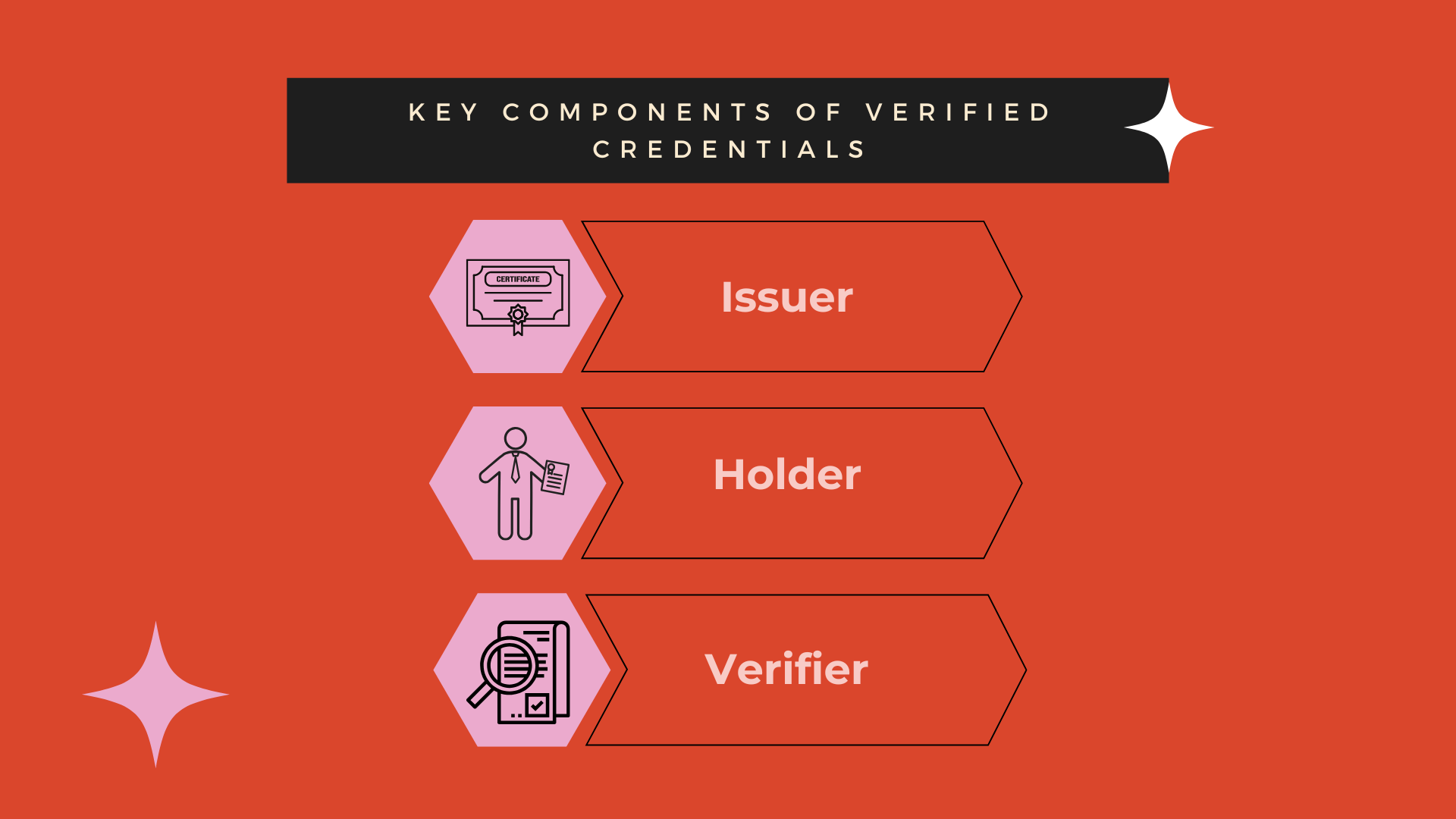
Key Components of Verified Credentials
At their heart, verified credentials function through a straightforward trust system involving three key participants:
- Issuer: A trusted organization, such as a university or employer, responsible for creating and issuing the credential.
- Holder: The individual who owns, manages, and decides when and with whom to share their credential.
- Verifier: The party, like a recruiter or government agency, that confirms the authenticity of the credential.
This triangular relationship ensures a seamless process where credentials are issued, held securely, and verified effortlessly, forming the backbone of trust in a digital ecosystem.

How Blockchain and Decentralized Identifiers (DIDs) Support Verified Credentials
Blockchain is the technology that ensures trust in verified credentials by providing an unchangeable record of every credential issued.
Once a credential is recorded on the blockchain, it cannot be altered or deleted, making it reliable and secure for anyone who needs to verify it. This gives both individuals and organizations confidence that the credentials they’re dealing with are accurate and tamper-proof.
Decentralized Identifiers (DIDs) add another layer of security by allowing individuals to control their own identity without needing to rely on central authorities like banks or governments.
Instead of having personal information stored in one centralized database, DIDs allow people to manage their credentials independently.
This combination of blockchain and DIDs ensures a more secure, transparent, and user-controlled way of verifying credentials that is ready for the future.
The Difference Between Centralized and Decentralized Identifiers
Traditional verification systems rely on central authorities, such as universities or employers, to store and manage data. This centralized approach can lead to delays, errors, and security breaches, as all records are stored in one place.
If this central system is compromised, it could expose sensitive information or disrupt the verification process.
Decentralized systems, however, give control back to the individual. Instead of relying on a central authority, people can manage their own credentials and share them securely.
This not only improves privacy but also enhances security, as there’s no single point of failure. By decentralizing the process, the system becomes more reliable, faster, and less prone to fraud or errors.
Use Cases of Verified Credentials
Verified credentials are transforming a wide range of industries by providing secure, efficient, and trustworthy ways to validate important information. Here are some key use cases across various sectors:
Verified Credentials in the Hiring Process
For recruiters, verified credentials are a game-changer. Instead of chasing references or verifying documents manually, they can authenticate a candidate’s qualifications in seconds.
This not only speeds up hiring but also ensures that only accurate and trustworthy information is considered.
Verified Credentials in Other Industries
Beyond hiring, verified credentials are transforming industries like healthcare, education, and finance, delivering practical benefits that were previously unimaginable. Here’s how:
- Healthcare: Patients can securely share vaccination records or medical histories with doctors and hospitals, enabling faster treatment and ensuring data accuracy.
- Education: Universities issue tamper-proof digital diplomas and transcripts, allowing graduates to effortlessly share their qualifications with potential employers or institutions.
- Finance: Banks and financial institutions use verified credentials to authenticate customer identities, ensuring compliance and reducing the risk of fraud.
- Travel: Digital health credentials, such as vaccination or test records, simplify border control processes and reduce delays at checkpoints.
These applications demonstrate the incredible versatility of verified credentials and their ability to enhance trust, security, and efficiency across industries.
How to Check the Authenticity of Verified Credentials
Verifying the authenticity of verified credentials is a simple and secure process. Here’s a step-by-step approach:
-
Obtain the Credential: The holder provides you with the credential link or a QR code to initiate the verification process. This could be for a diploma, work experience, certification, or other credentials.
Here’s an example of a sample digital credential - click here.
-
Scan the QR Code or Click the Link: If a QR code is provided, use a QR scanner or smartphone camera to scan it. Alternatively, click on the link to open the credential in your browser. Tool like The QR Code Generator ensures the code is high‑contrast, sized correctly, and placed so it’s easy to scan without compromising the credential design.
-
Access the Verification Platform: The link or QR code will take you to a verification platform that connects to the blockchain or decentralized database. This platform houses the cryptographic proofs needed to authenticate the credential. Each credential will have a unique ID, making sure that the credential is immutable and tamper-proof.
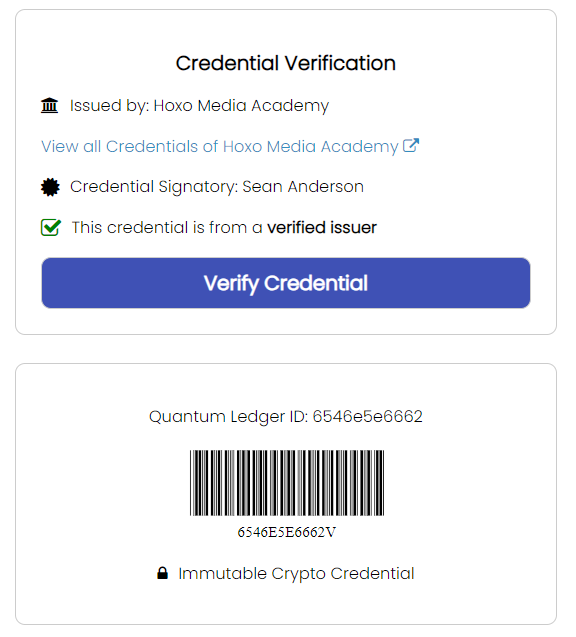
-
Check the Cryptographic Proofs: Over there, you can manually verify the credential by typing in the email address of the awardee. The system will then validate the cryptographic proofs associated with the credential, checking them against a secure, immutable record.
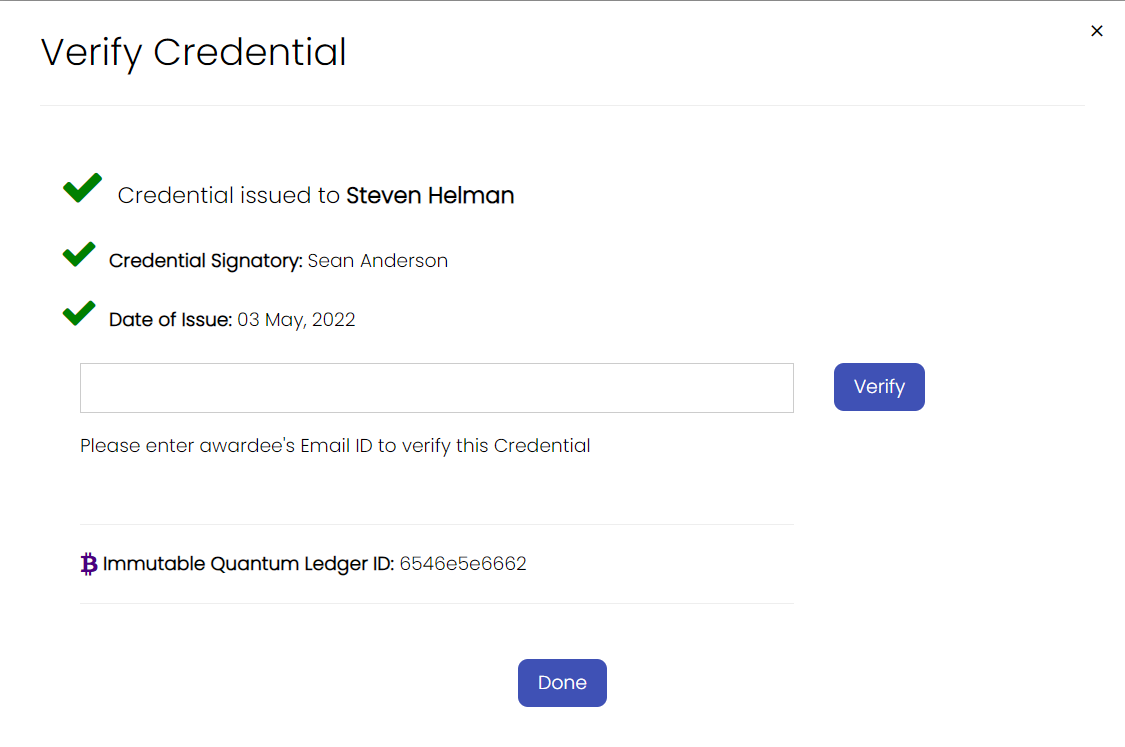
-
Verify the Issuer’s Identity: The platform will confirm whether the credential was issued by a trusted organization. It will also provide details about the credential’s authenticity.
-
Confirm the Credential’s Validity: If the proofs are verified, the system will confirm that the credential is valid and has not been tampered with. If the credential is invalid or altered, the system will alert you to the discrepancy.
-
Review the Results: The verifier receives a clear, real-time result indicating whether the credential is authentic. No intermediaries or manual checks are required.
These modern tools provide an efficient, accurate, and secure way to verify credentials, reducing human error, and ensuring a higher level of trust and transparency in the verification process.
CertifyMe’s Technology for Verified Credentials
By using blockchain technology, CertifyMe eliminates the risk of tampering, making it an incredibly secure method of verifying credentials.
The integration of verifiable signatures further strengthens this security, allowing issuers to cryptographically sign each document. This ensures that credentials can be verified quickly and without the need for intermediaries, significantly reducing the time and cost associated with traditional verification methods.
The Verified Credential Wallet offered by CertifyMe is designed for users to securely manage and share their credentials with ease. This digital wallet allows individuals to store all their verified credentials in one place and access them instantly.
With a simple interface, users can share their credentials with employers, educational institutions, or other relevant parties while maintaining full control over their personal information.
This combination of blockchain, verifiable signatures, and a secure wallet transforms how credentials are managed, making them more accessible, efficient, and trustworthy.
Criticisms and Concerns
While the potential of verified credentials is immense, there are challenges that need to be overcome.
One of the primary hurdles is the adoption of the technology across various industries. Many organizations may be hesitant to adopt new systems due to the upfront costs or the need to retrain staff.
Additionally, creating a standardized approach that works globally can take time, as different regions may have varying regulations or infrastructure requirements. However, as the demand for more secure and efficient credential verification grows, the momentum for widespread adoption is building.
Another significant concern revolves around privacy. Since verified credentials often involve sensitive personal information, ensuring data protection is paramount. While blockchain technology offers robust security, privacy concerns persist, especially regarding how personal data is stored and shared.
To address these concerns, ongoing advancements in encryption techniques and the development of privacy-focused technologies are making verified credentials safer to use.
These innovations are helping to strike a balance between transparency, security, and individual privacy, ensuring that verified credentials can be trusted and used with confidence worldwide.
Conclusion
Verified credentials are transforming the way we manage and verify important information, moving beyond the limitations of traditional systems. By using secure, digital solutions, they eliminate delays, reduce fraud, and enhance trust in sectors like education, healthcare, and employment.
The adoption of this technology provides individuals with greater control over their records, while organizations benefit from quicker, more accurate verifications. With a foundation in blockchain and decentralized identifiers, verified credentials are setting a new standard for how information is validated and shared in the digital world.
In my personal experience, CertifyMe stands out as a leader in the verified credentials space, offering a seamless and secure verification process. Their blockchain-powered system ensures that credentials are tamper-proof and easily verifiable with just a click. What sets CertifyMe apart is its focus on user privacy and the ease of access through the Verified Credential Wallet.
By leveraging cutting-edge technology, CertifyMe simplifies the process of sharing and authenticating credentials, making it a trusted solution for both individuals and organizations looking to embrace the future of digital verification. You can check out the benefits of using verified credentials through CertifyMe’s free trial by clicking here.

 Author :
Author : 




