Traditional credential management systems often struggle with issues like forgery, data mismanagement, and complex verification processes. Verifiable credentials (VCs) are designed to address these problems with a more secure and efficient approach.
In this blog, we’ll break down what verifiable credentials are, how they work, and why they’re rapidly becoming the gold standard for modern credentialing.
Understanding Verifiable Credentials
Verifiable credentials are digital documents that contain verified data about an individual, organization, or a thing. As the name suggests, a verifiable credential can be verified for its originality by anyone when shared by the recipient. Since verifiable credentials are tamper-proof, the information they carry cannot be altered.
What makes them different from traditional physical credentials, or even their digital equivalents, such as PDFs or other digital formats, is the way they are secured. A verifiable credential follows standards such as the W3C Verifiable Credentials standard or Open Badges 3.0, which are globally recognized frameworks for data integrity and security.
Essentially, a verifiable credential must contain specific attributes, such as metadata, a blockchain ledger, and cryptographic signatures, to prevent forgery or alteration as defined by W3C and Open Badges standards. In short, while a traditional document or PDF can be altered without the verifier’s knowledge, a verifiable credential prevents such tampering.
Why Do Verifiable Credentials Matter – The Benefits of Verifiable Credentials
Verifiable credentials offer a wide range of practical benefits for both issuers and recipients, making them a compelling alternative to traditional options. Below are some key reasons why verifiable credentials matter:
Tamper-Proof Security:
Since verifiable credentials are cryptographically signed and stored on secure infrastructure, they cannot be falsified or altered, while remaining verifiable.
Real-Time Verification:
Third parties, such as companies and organizations can instantly verify a credential’s authenticity without contacting the issuing organization. On the other hand, this is not possible with traditional credentials.
Automation and Efficiency:
Credential issuance and management processes can be automated to reduce manual effort and human error. With tools such as CertifyMe, organizations can issue hundreds of verifiable credentials within minutes and deliver them to recipients without any human intervention.
Easy Sharing and Visibility:
In most cases, credentials are meant to be shared or displayed. Verifiable credentials allow recipients to add them to LinkedIn profiles, resumes, email signatures, or digital portfolios, thereby enhancing visibility and discoverability.
The Working of a Verifiable Credential
Let us now look at how verifiable credentials function and why they are more secure than traditional systems. To begin, it is important to understand the parties involved in the verifiable credential lifecycle.
Parties Involved in a Verifiable Credential Model
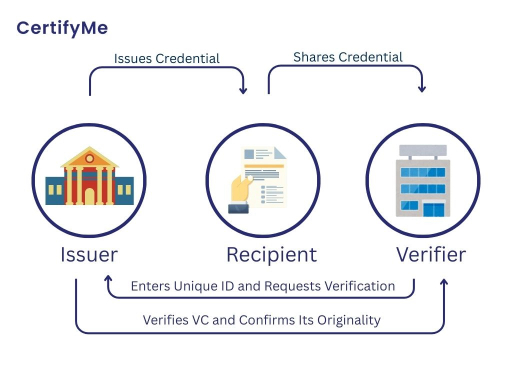
Consider the example of a student who receives a degree/credential from their university and later shares it with an employer during a job application. In this case, the parties involved are as follows:
The Issuer
It is the organization that issues the verifiable credential, in this case, the university. The issuer uses a digital credentialing software such as CertifyMe to create and issue the credential by entering the relevant recipient’s details. These details are referred to as metadata.
The Recipient
The student who receives the degree is the recipient. The recipient receives the credential via email, which includes a URL to access the verifiable credential. The recipient also receives access to a digital wallet, a secure space for storing verifiable credentials.
The Verifier
In this scenario, the verifier is the employer to whom the student has applied for a job. Once the student shares the digital degree, the employer can verify its authenticity through due procedure. For example, if the credential is issued using CertifyMe’s platform, the verifier can authenticate the credential through one of 3 ways :-
- Through ID-Tagging
- Through Cryptographic signatures
- Through OTP
Components of a Verifiable Credential
In addition to the parties involved, a verifiable credential consists of three main components:
Metadata: Metadata refers to verified information about the issuer, the recipient, and the credential itself. This data is not directly visible to third parties and is cryptographically signed to ensure security.
Claim: It is the statement that the verifiable credential makes about an individual, organization, or entity. For example, an academic degree serves as a claim that the recipient has completed a specific course of study.
Proofs: Proofs are the cryptographic and security mechanisms that protect the credential from forgery and enable verification of its originality when required.
Verifiable Credential Verification Process
Now that we understand the verifiable credential model, the verification process works as follows:
Blockchain Ledger
When the issuer creates a credential, it is anchored to a blockchain ledger. This ledger ensures immutability (permanence) while maintaining decentralization. Think of it as having multiple small boxes of information connected as nodes. If someone tries to edit information in one box, the other boxes will not accept the change.
Asymmetric Encryption
Another method used to verify a verifiable credential’s originality is asymmetric encryption, also known as a cryptographic signature.
This mechanism acts as a lock that protects the credential’s critical metadata from unauthorised third-party access. Only the issuer can unlock this information. When a verifier requests authentication, the issuer validates the credential against the blockchain ledger and confirms its authenticity.
This model enables verifiable credentials to function as a form of zero-knowledge proof, meaning the authenticity of a credential can be confirmed without revealing any personal information.
Use Cases of Verifiable Credentials
Verifiable credentials are transforming how organizations across industries issue, manage, and validate achievements and qualifications. Some of the most prominent use cases include:
-
Higher Education: Universities and colleges issue digital diplomas, transcripts, and certificates that can be instantly shared and verified by employers or other institutions.
-
Corporate Learning and Development (L&D): Organizations use digital badges and certificates to track employee skill development, training completion, and internal promotions.
-
E-learning Platforms: Online education providers award course completion certificates and micro-credentials that learners can showcase on professional networks and job platforms.
-
Professional Associations: Membership credentials, continuing education credits, and professional certifications are issued digitally to improve accessibility, renewal, and verification.
Conclusion
Upon reflection, it becomes clear that verifiable credentials represent a modern, secure, and efficient approach to issuing and validating achievements. As we continue to advance in an era of digitization, verifiable credentials are well-positioned to replace traditional credentialing systems.
As credentialing becomes increasingly digital and decentralized, understanding and adopting these secure systems will be essential for individuals and organizations seeking to remain credible and verifiable.
If you are looking to get started today, CertifyMe’s free plan offers an ideal entry point into getting acquainted with verifiable credentialing and how to implement it for your organization. For a much more customized and advanced verifiable credentialing system, talk to our team to get the right guidance and next steps.

 Author :
Author : 




